- twelsh0523
- May 19, 2025
- 4 min read
Updated: May 30, 2025
Aria Operations for Logs is a log management and analysis tool designed to collect, store, and analyze logs from various sources within an IT environment. It provides a centralized platform for managing and understanding logs generated by different applications and infrastructure components. There are also many content packs available at the VMware Marketplace. Each content pack includes specific dashboards, queries and events for different components within your infrastructure.
For this blog we will discuss how customers can use Aria Operations for Logs to aggregate logs from the infrastructure and forward particular events to a 3rd party SIEM due to security requirements. Let’s look at how to forward specific log entries.
First, we will start with the Windows Content Pack and the Security Overview dashboard.
1. Click Microsoft – Windows to expand the list of dashboards.
2. Click Security – Overview
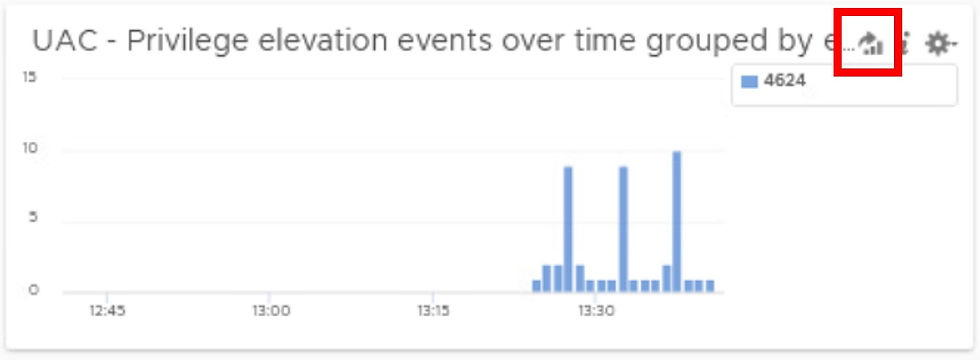
The Security – Overview dashboard shows several privileged events have occurred over the last hour.
1. Click the Explore Logs icon as shown to see the log events.
The Explore Logs allows you to see the log events in more detail. You can see the filters used for that dashboard. For the first example we want to expand the results, so remove the eventid and level filters.
1. Click the X in front of the eventid and the level lines to remove the filters.
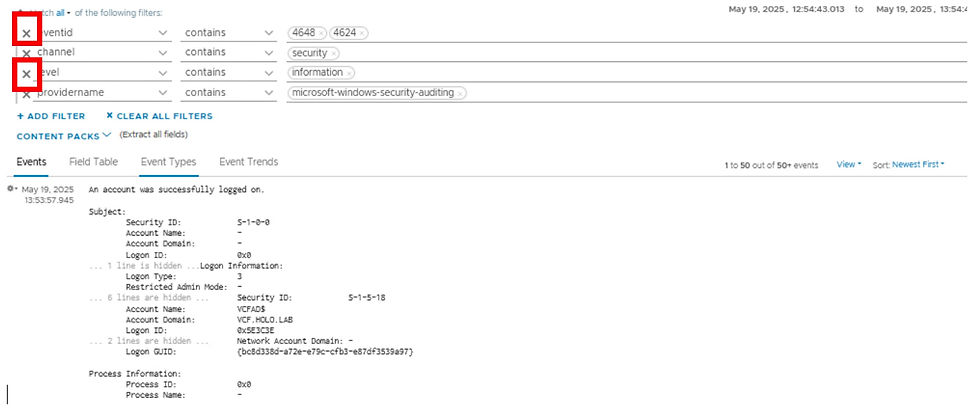
The results are log events that pertain to the Windows security channel and Windows security auditing. Now that we have the log events of interest, we will create the Log Forwarding filter.
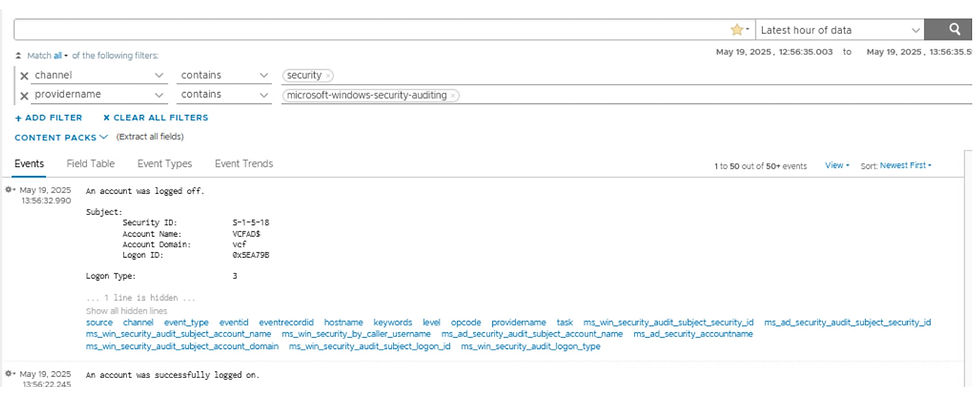
To create a Log Forwarding filter complete the following steps.
Click Log Management
Click Log Forwarding
Click + NEW DESTINATION
Fill out the New Destination dialog box for your environment. In my example, I have chosen the Syslog protocol, a optional Tag: msft=security for searching at the destination, the Transport UDP and included the 2 filters from the Explore page.
Click Run in Explore Logs Page to test the filters. This will open a new browser tab with the results.
Return to the original browser tab and click TEST to check the connection to your destination server.
Finally click SAVE

After a few minutes you should see logs are being forwarded to the destination server.

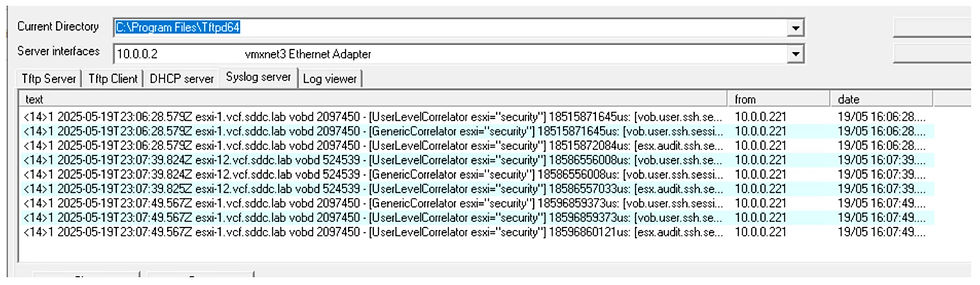
If we take a look at the destination Syslog server, we can see the forwarded events.

Now let's look at another use case where the fields don’t exist in the Log Forwarding Filters. This occurs because some fields are extracted after ingestion using regex. For this example, we will use the vSphere Content Pack.
Click VMware – vSphere to view the available dashboards for this content pack.
Click Security – Auditing to view the dashboard.
We will focus on the dashboard widget which shows ssh sessions which have been opened, closed and failed.
1. Click the Explore Logs icon to view the individual events.
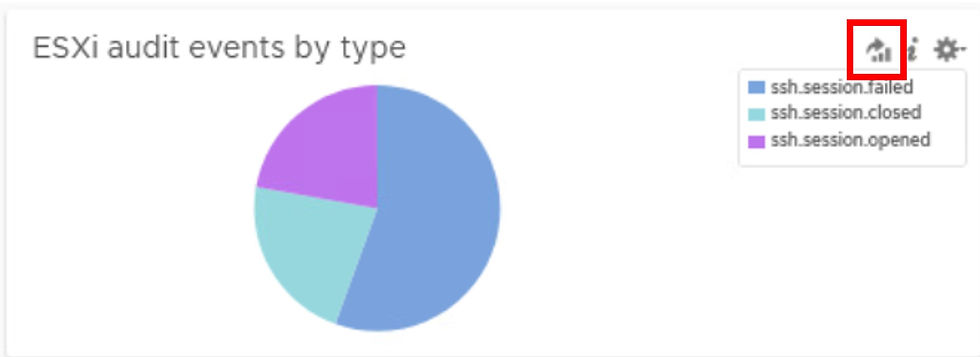
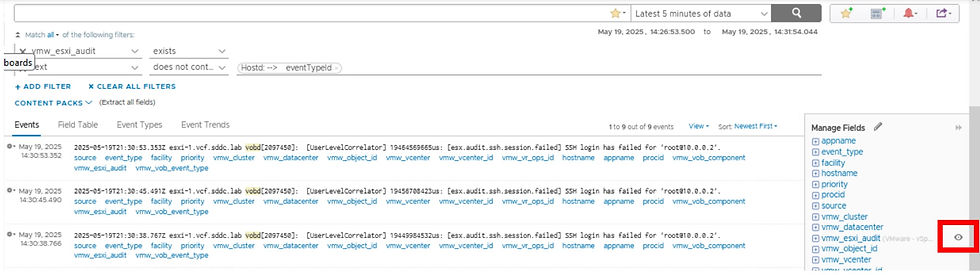
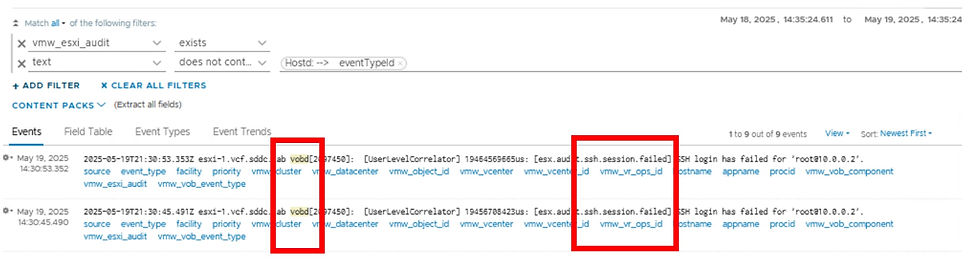
The results are 9 entries for ssh events. The “vmw_esxi_audit” filter is an example of a filter generated after ingestion using regex. We easiest way to identify fields created via regex is in the manage fields list. Look for the “View this field” icon as shown.
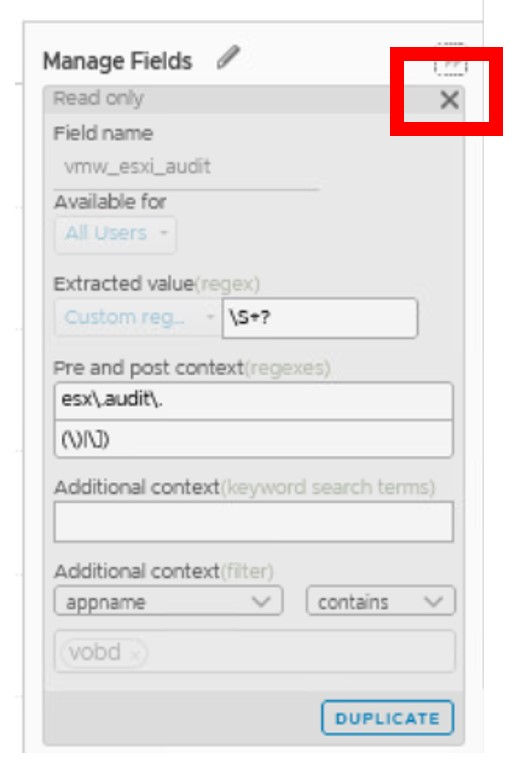
1. Click View this field to see the regex that was used to generate this field.
1. Click the X to close the Manage Fields dialog box.
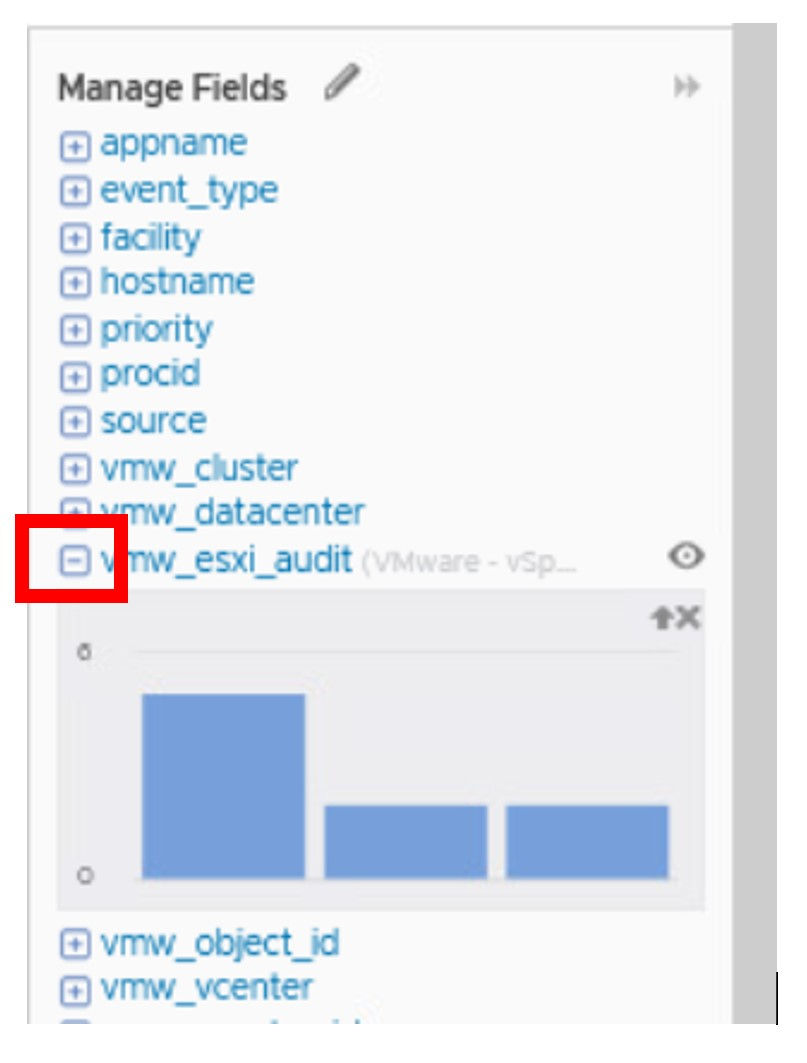
There are 3 event types for the “vmw_esxi_audit” field.
Click the + to expand the field. If you hover over each of the bars you will find the event types correlate to opened, closed and failed ssh sessions.
So now we are ready to create the Log forwarding filter. Let’s go back to Log Forwarding.
Click the CLONE icon to save time filling out all of the fields.
Enter a new name and change the optionable tag field.
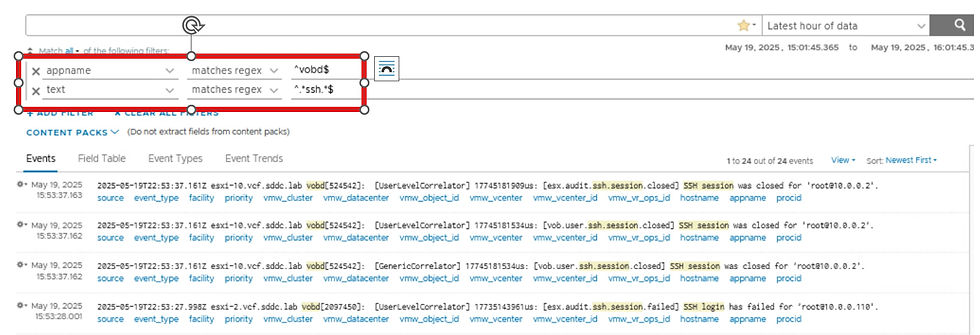
Click + ADD FILTER and start typing vmw_esxi. You will notice “vmw_esxi_audit” doesn’t exist in the available filter fields. As mentioned earlier, this is because that field is extracted after ingestion using regex. In these situations we need to create the Log Forwarding filter based on text matching.
Click CANCEL

Return to the ESXi Audit Events by Type widget and then the Explore Logs icon as before to view the same events.
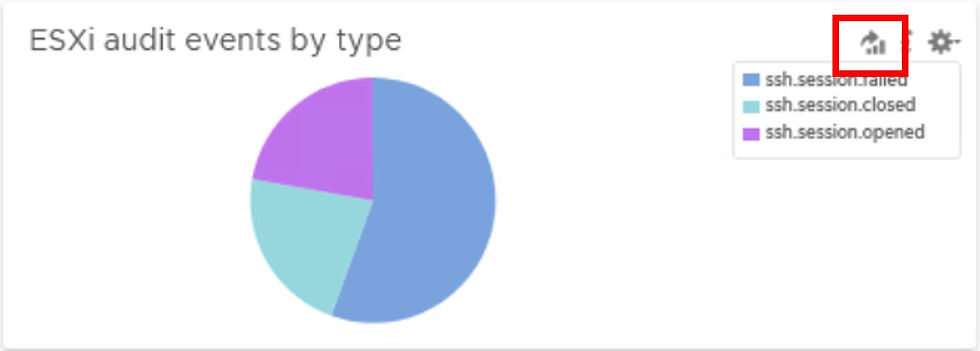
When reviewing the 9 events there are some fields that are common across the events. These can be used for filters. The first filter will be appname =“vobd” and also we can use the text “ssh”
Return to Log Forwarding and create a destination as shown below. Note: For the text filter we have entered "*ssh*"
Click Run in Explore Logs page to check your filters are returning the expected events.

When you click Run in Explore Logs Pane you will notice the regex setting for the defined filters. Go back to the original browser tab and SAVE the forwarding filter.
After a few minutes the destinations page will display the number of events forwarded to the destination server.
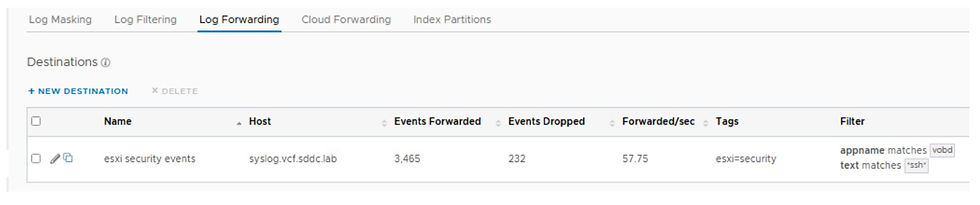
To verify if all is working, go to your destination server and view the results of the event forwarding. Also notice the optional tag is included for each event which can be used for searching at the destination server.
I hope you found this information helpful when working with Aria Operations with Logs.
